 One of the things that makes the Internet so intriguing is the staggering amount of information a person has access to. If you are reading this article, there is a good chance you know how to utilize popular search engines like Google, Ask, and Bing to obtain information. While these engines are powerful and have charted a great deal of the Internet, much remains uncharted. For over nine years, a hidden Internet has existed, and has become known as the Darknet/Deepweb.
One of the things that makes the Internet so intriguing is the staggering amount of information a person has access to. If you are reading this article, there is a good chance you know how to utilize popular search engines like Google, Ask, and Bing to obtain information. While these engines are powerful and have charted a great deal of the Internet, much remains uncharted. For over nine years, a hidden Internet has existed, and has become known as the Darknet/Deepweb.
There are a few things you need to understand about the Darknet/Deepweb before diving into it.
- The purpose of the Darknet is anonymity. Anonymity is actually required just to gain access. Therefore, no one on the network can identify you, and you can identify no one else on the network.
- The Darknet is built on a Peer-to-Peer backbone. By this, I mean content is not centrally hosted. It is “shared” between peers using non-standard ports and protocols.
- Darknet sites are completely inaccessible unless you are routing traffic through an anonymizing network such as TOR or I2P.
- While there is a considerable amount of useful information on the Darknet, there is also tons of illegal activity within. Do not click links or download material you are unsure about.
What type of information is on the Darknet?
You can find anything from political advocacy blogs to leaked documents and controversial essays from freelance journalists. However, there is also a lot of bad stuff too. Because this network requires anonymity, it has unfortunately attracted many unsavory types. Child pornography, stolen passwords, and exploit kits can all be bought, sold, or downloaded from this network. Once again, use with discretion.
How do I access it?
You would imagine that an underground network such as the Darknet would be quite difficult to access. In fact, it is not. It is extremely easy to gain entry. This is because the true security of this network is the decentralized threat model of anonymity engines like TOR and I2P. By this, no one on the network can identify anyone else on the network, because of the way information is passed between peers.
There are several ways you can get online. To keep this article short and concise, I will be using the most straight-forward method: TOR. Firstly, navigate to TOR’s official website and grab a free copy of the TOR browser bundle. This will be your key to get in.
Once you have downloaded the binary, simply run through the installation wizard. Once installed, execute TorBrowser.
Simply click “Connect” and wait for the TOR circuit to be established.
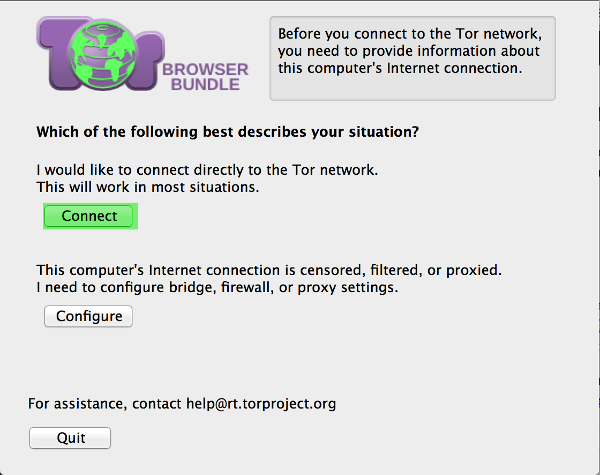
Once this is done, a modified Firefox web browser will pop up. From here, you can access any site completely anonymously. Besides hiding your IP through a complicated network of onion routers, TorBrowser will also hide things about your browser session such as the operating system you are using and referral pages.
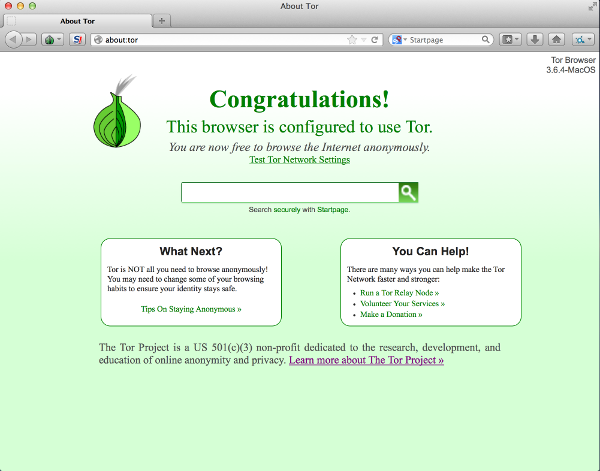
Navigating the Darknet/Deepweb
Congratulations! If you have made it this far, you have everything you need to access the hidden crevices of the Internet, well almost. You still need a roadmap. A good start is “The hidden Wiki,” which can be found by navigating to this link http://jh32yv5zgayyyts3.onion (the link is always changing, so there is no guarantee that this link will work in the future) in your TorBrowser. You can learn more about the Hidden Wiki here.
Disclaimer: The content of this article is for informational and educational purposes only. There is plenty of offensive, uncensored and illegal content in the darknet. Venture at your own discretion.
Closing Thoughts
Several times throughout this article, I have stated “use discretion;” I will do so once again. Keep in mind the basic guidelines to Internet safety and apply them doubly when surfing the Darknet.
- Do not disclose your identity to anyone under any circumstances.
- Assume any content you download is malicious, unless you absolutely trust the source, which you shouldn’t in the darknet.
- If you do download a binary, scan it with your antivirus before execution.
The post What is the Darknet? appeared first on Make Tech Easier.
![]()




















No Comments